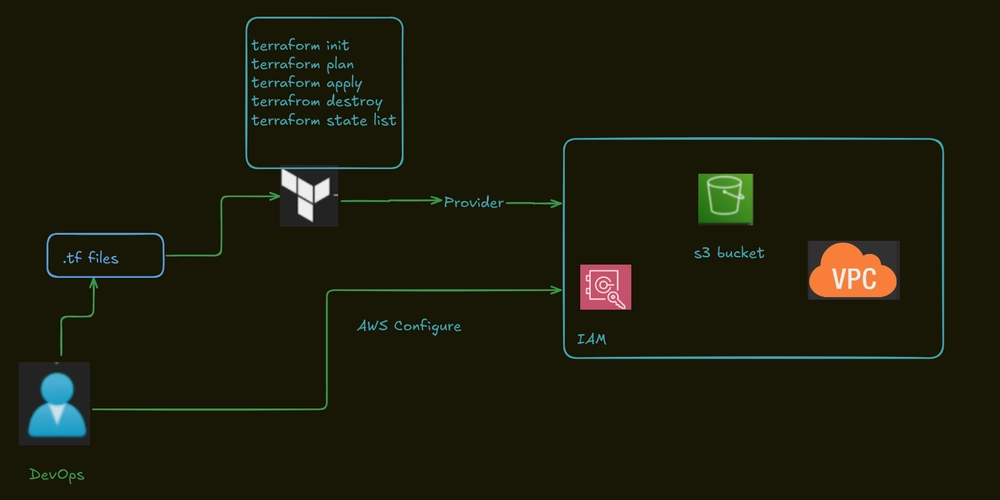
Creating IAM User, S3 Bucket and VPC
Infrastructure as Code has completely changed how cloud resources are created and managed. Terraform enables you to deploy AWS services using simple, declarative configuration files. This article explains how Terraform interacts with AWS, how authentication works, and how to create both a VPC and an S3 bucket with an implicit dependency between them.
1. Authentication With AWS
Terraform uses the AWS provider to communicate with AWS services. The provider needs valid credentials, which can be configured in several ways:
- Using the
aws configurecommand to store credentials inside~/.aws/credentials - Setting environment variables such as
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY - Using IAM roles when running Terraform from EC2, ECS, or Lambda
- Using AWS SSO or shared credentials files
The IAM user or role must have permissions like:
ec2:CreateVpc
ec2:Describe*
s3:CreateBucket
s3:PutBucketTagging
Terraform will use these credentials to authenticate and perform actions on AWS.
2. What Is an AWS VPC?
A Virtual Private Cloud is your own isolated network environment inside AWS. It allows you to define:
- IP address ranges (CIDR blocks)
- Public and private subnets
- Route tables
- Gateways
- Security boundaries for workloads
The configuration in this example uses the CIDR block:
10.0.0.0/16
This provides a large IP space to create multiple subnets and services.
3. What Is Amazon S3?
Amazon S3 is a highly durable object storage service. It is commonly used for:
- Application data
- Logs and backups
- Static website hosting
- Big data pipelines
Important points to note:
- Bucket names must be globally unique
- Buckets store objects with unlimited scalability
- Tags help in managing and identifying buckets
To avoid naming conflicts, we use a random suffix generated by Terraform.
4. Terraform Code to Create a VPC and S3 Buckets
Below is the Terraform configuration that provisions:
- A VPC
- An S3 bucket with a random suffix
- Another S3 bucket that relies implicitly on the VPC
- Outputs showing resource IDs
This demonstrates how Terraform builds dependencies using references.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 6.0"
}
}
}
provider "aws" {
region = "ap-south-1"
}
resource "random_id" "suffix" {
byte_length = 4
}
resource "aws_s3_bucket" "bucket1" {
bucket = "bucket1-${random_id.suffix.hex}"
tags = {
Name = "My bucket 2.0"
Environment = "Dev"
}
}
resource "aws_vpc" "main_vpc" {
cidr_block = "10.0.0.0/16"
tags = {
Name = "main_vpc"
Environment = "Dev"
}
}
resource "aws_s3_bucket" "bucket2" {
bucket = "bucket12345-${aws_vpc.main_vpc.id}"
tags = {
Name = "bucket2"
VpcLinkedTo = aws_vpc.main_vpc.id
}
}
output "resource_ids" {
value = {
vpc_id = aws_vpc.main_vpc.id
s3_bucket_id = aws_s3_bucket.bucket2.id
}
}
5. How Implicit Dependency Works in Terraform
Terraform automatically understands resource dependencies without requiring depends_on when one resource references another.
For example:
bucket = "bucket12345-${aws_vpc.main_vpc.id}"
This tells Terraform:
- The VPC must exist before the bucket is created
- The bucket depends on the VPC by reference
Terraform builds a dependency graph internally and always provisions resources in the correct order.
6. What Happens During terraform apply
When you run:
terraform init
terraform apply
Terraform performs the following sequence:
- Validates the configuration
- Authenticates using the AWS provider
- Generates the random ID
- Creates the VPC
- Creates the first S3 bucket
- Creates the second S3 bucket that depends on the VPC
- Prints the output values
This ensures a consistent setup every time you apply the configuration.
7. Reference Video
This video demonstrates the exact workflow covered in the article.